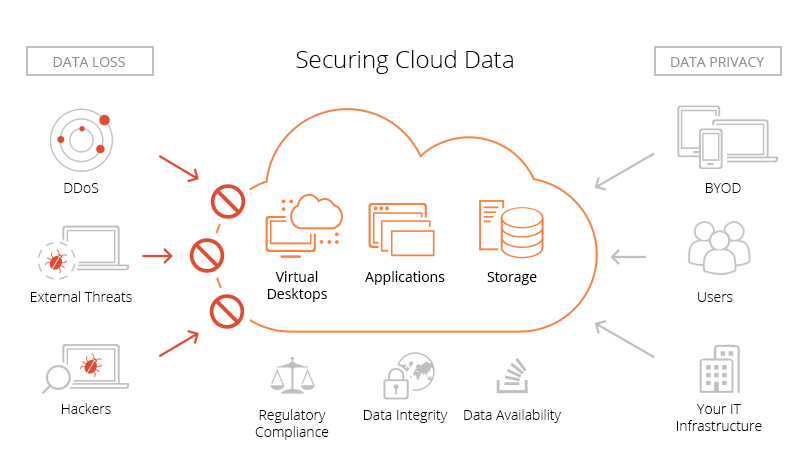
Today, almost everyone is using the cloud infrastructure whether it is for data storage, infrastructure, or services. With a large number of entities present on the cloud, the potential vulnerabilities increase significantly. The importance of the cloud in digital transformation goals has made the role of security procedures to fight internal and external threats more important than ever.
Contents
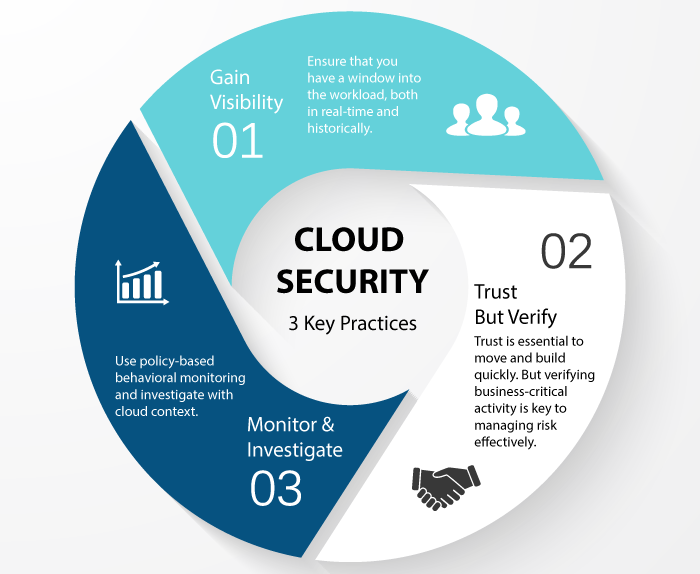
What is cloud security and why is it important?
The discipline of cyber security responsible for securing the cloud computing environment is known as cloud security. Essentially cloud security has the same goals as cybersecurity. Cloud security is aimed at protecting data, infrastructure, and applications on the cloud. It requires the administrator to protect data on a third party’s infrastructure.
Today, enterprises are transitioning to cloud-based environments at unimaginable speeds. As per estimates, the worldwide public cloud services market is set to grow by 20.4% in 2022.
The migration of data and business content on the cloud has IT professionals concerned because of the security and governance of the cloud environment. Protecting customer data is crucial for building trust for the service providers. Cloud security is crucial because of the following reasons:
- Cost optimization: The presence of security measures from the onset saves cost by reducing the amount of rework needed to build in additional measures.
- Manages remote work: Security measures are essential for supporting hybrid work environments. It becomes more important to protect data when employees are accessing it using the public internet.
- Disaster recovery: Cloud security services are a proactive approach. Cloud-based security ensures protection against accidental and malicious attacks.
- Compliance requirements: Cloud-based security solutions ensure that the companies are in line with regulatory requirements like HIPPA and GDPR.
Types of cloud services
Cloud services have evolved into different models each with a specific strategy to meet user requirements. The level of control, flexibility, and management vary with each type of cloud service. There are mainly three cloud services:
- Platform as a service (PaaS) – It is a cloud service solution that allows the organization to focus on the deployment and management of applications by eliminating the need to manage the need hardware and software systems. This builds more efficiency in the deployment process.
- Infrastructure as a service (IaaS) – It is a cloud service that requires us to pay for cloud computing, storage, and networking resources based on our usage. The pay-as-you-go basis provides the highest level of flexibility and efficiency in managing the organization’s IT resources.
- Software as a service (SaaS) – The cloud service provider hosts the applications in this model and makes them available to the end-users. The customers only need to identify how they are going to use the application and don’t have to worry about how the infrastructure is managed or deployed.
Cloud security vs traditional network security
Tradition network security and cloud security differ in certain aspects. The access in traditional network security is controlled using a perimeter model. Whereas the cloud environment is highly connected and makes it much easier to pass the security measures at the perimeter.
In the case of cloud security, everything is software and the cloud-based security solutions need to respond to environmental changes through cloud-based management systems or application processing interfaces (APIs) to cater to the dynamic environment.
Apart from that one thing that distinguishes cloud security from traditional network security is that cloud security is a shared responsibility. Using a cloud environment maintained by a third party doesn’t give us the liberty to sit back and relax but requires us to maintain the same due diligence to protect against security threats.
Benefits of cloud security solutions
Cloud security solutions solve business concerns of working in the cloud environment by providing the following benefits:
- 24*7 visibility – Cloud-based security solutions like Apptana enable round-the-clock monitoring of cloud resources and provide live updates on the security posture.
- Subscription model – Usually cloud security services have a pay-as-you-go model which requires us to only pay for the resources that we are using.
- Prevention from DDos attacks – Distributed denial of service attacks is a security threat that inhibits the ability of the system to respond to genuine user requests. DDoS mitigation solutions come with constant monitoring and real-time updates against such attacks.
- Adapt to business needs – With comprehensive cloud-based security solutions in place businesses can easily incorporate new products and services into their infrastructure to which the security measures can easily adapt.
- Meet legal compliance – Cloud security has different requirements across sectors. The extent of requirements varies depending upon the amount of personal and financial data being managed.
Challenges of cloud security solutions
Due to the large scale and flexibility of the cloud environment, implementing security solutions in the cloud environment face numerous challenges. Some of them are as follows:
- Maintaining a track: Since the data on the cloud is accessed outside the corporate networks on numerous occasions maintaining a record of the data access is difficult.
- Multitenancy: Multiple infrastructures are hosted on the public cloud. So, the risk of the cloud environment being compromised by malicious attacks increases significantly.
- IT expertise: Many organizations identify the lack of knowledge and expertise in dealing with cloud environments as a barrier to implementing cloud-based security solutions. Cloud experts along with resources with knowledge of particular cloud aspects are needed to overcome this barrier.
- Misconfigurations: Default settings in the cloud environment also result in privacy and data breaches. Misconfigurations include not resetting default passwords, updating privacy settings, etc.
- Insecure APIs: A cloud environment has multiple attack points. One potential threat area is an unsecured API. Hackers can intrude and access data through unsecured APIs as well which makes it important to ensure that the API layer is also fully protected.
Why opt for cloud-based solutions now and for the future?
The adoption of cloud computing services is what is going to help industries and enterprises stay relevant after the massive wave of digital transformation that the world is experiencing. It is expected that 90% of companies with more than 1000 employees will shift to cloud environments by 2024.
Now more than ever it is agreed that the cloud is not an innovative choice for businesses but a necessity. It has become a necessity because of the speed and agility attached to the service. Businesses can respond to changes and make decisions by collaborating across regions with the help of the cloud. Cloud-based solutions are a major driver of innovation. They support automation which ultimately drives innovation and efficiency in enterprises.
Another important factor driving organizations to adopt the cloud is cost optimization achieved by the technology. The technology enables seamless collaboration between employees across regions. Thus, adopting the cloud helps organizations prepare for the future of workspaces.
Taking into consideration the numerous innovative potential that cloud-based solutions equip an organization with, there is no doubt that the right time to adopt them is now!
FAQs
What is cloud security?
Cloud security is a discipline of cybersecurity that encompasses a set of policies, procedures, and practices to protect the cloud environments that organizations operate in. Cloud-based security solutions help in the protection of privacy and data that is stored on various cloud platforms.
Why is cloud security important?
Cloud computing services are no longer seen as the future but they are seen as a necessity by enterprises to tackle large-scale digital disruption. But to ensure that enterprises continue to trust the cloud and keep shifting to it, we have to ensure that the environment is protected from malicious attacks. Cloud security solutions are needed to ensure that the business data remains safe and there is no privacy breach.
What are the four pillars of cloud security?
The four areas of cloud security are:
- Compute based security
- Visibility and compliance
- Identity security
- Network protections.
What is a cloud security framework?
Cloud security frameworks provide the benchmark practices in implementing cloud-based solutions. Some of them are:
- NIST’s cybersecurity framework
- FedRAMP
- Cloud Security Alliance’s cloud control matrix.